Thought Leadership
Can You Really Protect Yourself From Invoice Fraud?
July 19, 2021


This post was originally published on Information and Data Management Magazine
As Australia continues to slip in and out of lockdowns, business continuity continues to be tested. While business leaders battle to try and not just survive the pandemic but thrive, there are a groups of highly sophisticated scammers seeking to exploit the pandemic and scam businesses out of their hard earned and much needed cash. According to the ACCC’s latest Targeting Scams Report businesses lost over $128m to business email compromise scams – thats nearly $2.5m a week.
“Small and micro businesses made most of the reports to Scamwatch and experienced an increase in losses in 2020, although larger businesses reported the highest losses,”
ACCC Deputy Chair Mick Keogh
invoice fraud leads the way
According to data from Scamwatch, false billing scams were the most commonly reported scam and accounted for over 75% of total losses to businesses. The number of reported scams has jumped by 44% over the last year as scammers take advantage of both the confusion and disruption caused by the pandemic. Scammers are also getting better at what they do with total invoice fraud losses that are reported jumping by 180% in the same time period.
types of invoice fraud
There are a number of different invoice fraud happening in the market right now, here are a few examples:
Updated Bank Account Details
You get an email from your supplier asking to update their bank account details due to a change in their internal systems and processes and you update it accordingly. Unfortunately, the email address of your supplier has been compromised by a scammer and you’ve just changed the bank account details of your supplier to that of a scammer. Your suppliers invoice comes in for a legitimate piece of work which you process and pay, the money never gets to your supplier. This same situation happened to John at a local manufacturing business and it cost his business $17,000.
Unknown Supplier Invoice
You are sent what looks like a legitimate invoice from a company that you don’t have set up in your ERP, as the invoice looks legitimate it gets passed around the business to see if belongs to anyone. Someone mistakenly claims the invoice and processes it for approval and the invoice gets paid. This type of basic invoice fraud was extremely popular a number of years ago
Intercepted and Changed Invoice
Scammers intercept legitimate invoices sent via email and change the payment details to include fraudulent payment information. You receive the invoice and process it as normal, paying the invoice not realising you have been scammed. This is now one of the most common ways in which businesses are being scammed and is a very sophisticated and difficult one to manage.
but we wouldn’t fall for invoices scams…would we?
According to MineralTree, 68% of executives reported that they had received a fake invoice or experienced some other attempted form of payments fraud – that’s 2 out of 3 executives. Most businesses have processes in place to ensure they can protect themselves from invoice fraud and digital invoice processing and accounts payable automation claim to solve this problem. Let’s look at a typical process for invoice processing:
- Digital invoice receipt usually via email
- Basic Invoice data is captured automatically to varying degrees
- Basic data validation for duplication and active suppliers
- Invoice is routed to a reviewer for review and account coding
- Invoice is the routed to an approver for final approval
- Invoice is processed through for payment
Sounds robust? It’s really only reducing the risk of duplicate payments and payments to suppliers that don’t exist in your system. However, if you ran an intercepted and changed invoice scam through this same process where the invoice is intercepted before it gets to you and the bank account details are changed – it wouldn’t get picked up.
so, how can businesses really protect themselves against invoice fraud?
Businesses looking to truly protect themselves against invoice fraud can have a few options:
- Add more manual invoice validation checks prior to processing
- Automate invoice validation checks before the invoices are processed
- Move invoicing into the secure Peppol e-invoicing network.
Add more manual invoice validation checks
To try and mitigate the risk of invoice fraud you could add a series of manual invoice validation checks. These checks would depend on your own processes but we would recommend:
- External supplier validation – manually checking that a supplier is legitimate, through website checks/calling etc.
- Business Number validation – manually checking business numbers are accurate and relate to the supplier on the invoice (e.g. ABN checks).
- Internal supplier details validations – manually checking whether the supplier details on the invoice match your master supplier records.
- Duplicate check – manually checking you have not received this invoice from this supplier before
- Purchase order matching – manually identifying whether the invoice references a purchase order, and whether the supplier and purchase details match what is on the invoice.
- Bank account verification – manually validating that the bank account listed on the invoice matches the one in your supplier records.
This can all add significant time and cost to your invoice processing workflow and is prone to human error. Fortunately all of these can be automated.
Automate invoice validation checks before the invoices are processed
With modern AP automation and procure to pay automation tools, data verification of invoice data can completely automated and mitigate the risk of invoice fraud. The checks highlighted above can be automated and enhanced through adopting the right technology:
- External supplier validation – making automated checks against popular risk and fraud databases to ensure your suppliers are legitimate like Dun and Bradstreet.
- Business Number validation – making automated checks against Government business records to ensure the business is who they say they are
- Internal supplier details validations – automatically checking whether the supplier details on the invoice match your master supplier records.
- Duplicate check – automatically making sure you have not received this invoice or an invoice very similar from this supplier before
- Purchase order matching – automatically identifying whether the invoice references a purchase order, and whether the supplier and purchase details match what is on the invoice and automatically importing the PO approval if it matches
- Bank account verification – automatically validating that the bank account listed on the invoice matches the one in your supplier records.
Each of the above methods are effective ways to mitigate invoice fraud. However, a third option is gaining a lot of traction across the region.
Move invoicing into the secure Peppol e-invoicing network.
Electronic invoicing (or e-invoicing) is the automated digital exchange of invoice information directly between a buyer’s and supplier’s systems, removing the need for any manual data entry or validation. The ATO estimate that it can reduce the cost of processing an invoice down to $9.18.
Australia, New Zealand and Singapore have all adopted a globally recognised standard for sending e-invoices and e-orders known Peppol (Pan-European Public Procurement OnLine). This standard enables anyone who is part of the network to easily and safely, send e-invoices and e-orders to each other. The standard also enables a simple and accessible way for businesses to be onboarded onto the network. There are already 200,000+ businesses across 34+ countries on the Peppol network.
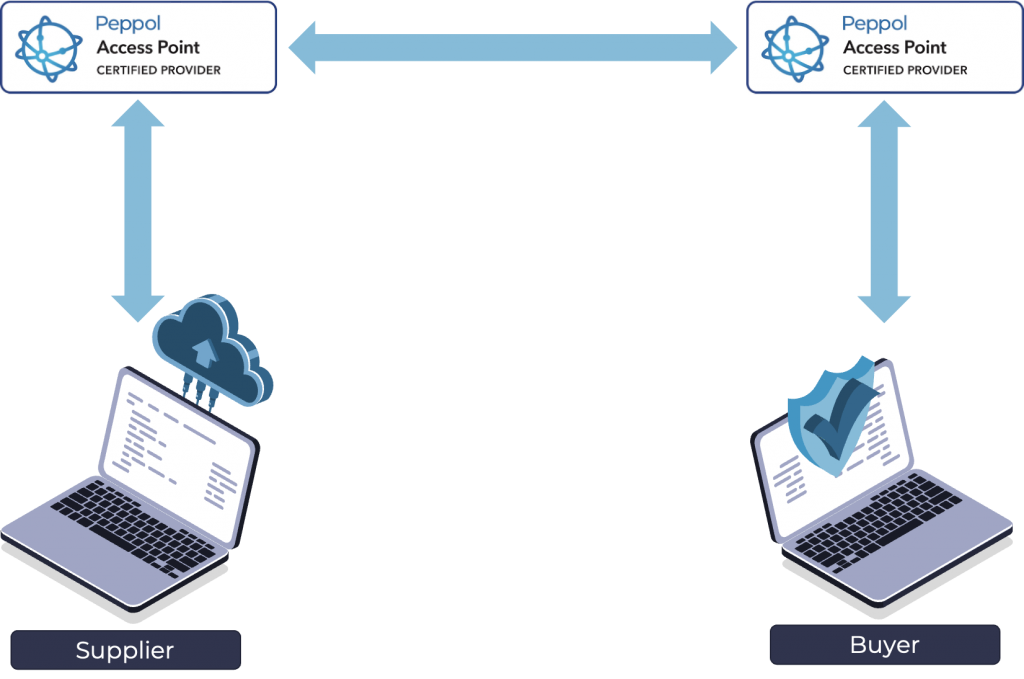
How does Peppol e-invoicing work?
Peppol e-invoicing works by suppliers and buyers sending their invoices or orders through their systems to their certified Peppol Access Point. The Access Point verifies the data on the invoice or order and then sends it on to the receivers certified Access Point who transmits the data into their system. This means that data is shared almost instantly into the receivers system without any manual data entry or manipulation required.
Several mandates are upcoming for Australian federal and state government agencies and businesses to switch to Peppol e-invoicing.
Eliminate Invoice Fraud with Peppol
We validate that the sender is who they say they are and that bank account details match your records before transmitting the data through the Peppol network. The network itself is highly secure as only accredited Peppol Access Points providers like Valtatech can exchange the documents over the Peppol network. Access providers like us are required to meet strict security protocols equivalent to ISO27001 covering intrusion prevention, multi-factor authentication for privileged user access and data encryption to ensure the security of the network.